An Exchange hybrid deployment is a way to extend the feature-rich experience and administrative control of an on-premises Microsoft Exchange organization to the cloud. It provides a seamless look and feel of a single Exchange organization between an on-premises Exchange organization and Exchange Online.
Monday, July 31, 2023
How to setup Azure AD Connect cloud sync to your Organization
StandardMonday, July 17, 2023
All you need to know about Remote Help with MS Intune
Standard
Prerequisites
- Intune subscription
- Remote Help add on license or an Intune Suite license for all IT support workers (helpers) and users (sharers)
- Windows 10/11
- The Remote Help app for Windows.(https://aka.ms/downloadremotehelp)
Network Requirement
| Domain/Name | Description |
|---|---|
| *.aria.microsoft.com | Used for accessibility features within the app |
| *.events.data.microsoft.com | Microsoft Telemetry Service |
| *.monitor.azure.com | Required for telemetry and remote service initialization |
| *.support.services.microsoft.com | Primary endpoint used for the Remote Help application |
| *.trouter.skype.com | Used for Azure Communication Service for chat and connection between parties |
| *.aadcdn.msauth.net | Required for logging in to the application Microsoft Azure Active Directory (Azure AD) |
| *.aadcdn.msftauth.net | Required for logging in to the application Azure AD |
| *.edge.skype.com | Used for Azure Communication Service for chat and connection between parties |
| *.graph.microsoft.com | Used for connecting to the Microsoft Graph service |
| *.login.microsoftonline.com | Required for Microsoft sign in service. Might not be available in preview in all markets or for all localizations |
| *.remoteassistanceprodacs.communication.azure.com | Used for Azure Communication Service for chat and connection between parties |
| Allowlist for Microsoft Edge endpoints | The app uses Microsoft Edge WebView2 browser control. This article identifies the domain URLs that you need to add to the allowlist to ensure communications through firewalls and other security mechanisms |
Check for Licensing
- Access the Intune portal.
- Navigate to the Endpoint portal.
- Proceed to the Tenant Administration section.
- Select "Intune Add-ons" to check the licensing.
Integrate Intune - Remote Help
- Access the Endpoint portal.
- Navigate to the Tenant Administration section.
- Choose "Remote Help" from the available options.
- Click on "Settings" and select "Configure.
- Access the Endpoint portal.
- Navigate to the Tenant Administration section.
- Choose "Roles" from the available options.
- Name : Provide a Name
- In the permission select Remote help and select necessary permission
- Elevation - Elevation allows the helper to enter UAC credentials when prompted on the sharer’s device when remote help is enabled. Enabling elevation also allows the helper to view and control the sharer’s device when the sharer grants the helper access.
- View Screen - View screen allows the helper to view the sharer’s device when Remote Help is enabled for all platforms we support.
- Take Full Control - For Windows and Android devices, take full control allows the helper to view and control the sharer’s device when Remote Help is enabled.
- Select next & Create.
- Select Assign and provide a name
- Admin Group - Add the admin group or helper group (Support team Group)
- Scope Group - you can add all users, All device or specific halpee group.
Deploy Remote help app though Intune
- Remote app for windows - (https://aka.ms/downloadremotehelp)
- Microsoft Win32 Content Prep Tool - https://github.com/Microsoft/Microsoft-Win32-Content-Prep-Tool
- specify the source folder of the Remote app for windows location
- Specify the setup file - Example - remotehelpinstaller.exe
- Specify the output folder to export the intunewin file
- Catalog Select - No
- App Type : Windows app (Win32) and select
- Click Select App package and brouse the intunewin file we created previously
- file the app information as required & click next (publisher required to fill
- Install command - remotehelpinstaller.exe /quiet acceptTerms=1
- Uninstall command - remotehelpinstaller.exe /uninstall /quiet acceptTerms=1
- Operating system architecture - 32 bit & 64 bit
- Minimum operating system - Windows 10 1607
- Rules format - Manually configure detection rules and click +add
- Rule type - select File
- Path, specify C:\Program Files\Remote Help
- File or folder, specify RemoteHelp.exe
- Detection method, select String (version)
- Operator, select Greater than or equal to
- Value, specify the version of Remote Help you are deploying. For example, 10.0.22467.1000
- Leave Associated with a 32-bit app on 64-bit clients set to No
Setting up Conditional Access for Remote Help
- Install-Module -Name AzureADPreview
- Connect-AzureAD
- New-AzureADServicePrincipal -AppId 1dee7b72-b80d-4e56-933d-8b6b04f9a3e2
Create policy
- Access the Endpoint portal.
- Navigate to the Endpoint security section.
- Select Conditional Access
- then select Policy and Create New policy
Wednesday, July 12, 2023
System-preferred multifactor authentication Method
StandardSystem-preferred multifactor authentication (MFA) is a security feature that prompts users to sign in using the most secure method they have registered. This can help to improve sign-in security and discourage the use of less secure methods, such as SMS.
For example, if a user has registered both SMS and Microsoft Authenticator push notifications as MFA methods, system-preferred MFA will prompt them to sign in using the push notification method. The user can still choose to sign in using another method, but they will be first prompted to try the most secure method they have registered.
If you are an administrator, I encourage you to consider enabling system-preferred MFA in your organization. This is a simple way to improve the security of your sign-in process and protect your users' data.
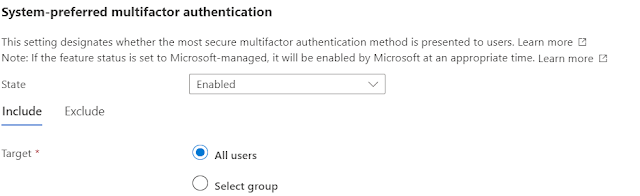
Enable system-preferred MFA in the Entra ID portal
In the Azure portal, click Security > Authentication methods > Settings.
For System-preferred multifactor authentication, choose whether to explicitly enable or disable the feature, and include or exclude any users. Excluded groups take precedence over include groups.
How does system-preferred MFA determine the most secure method?
When a user signs in, the authentication process checks which authentication methods are registered for the user. The user is then prompted to sign in with the most secure method according to the following order. The order of authentication methods is dynamic, meaning it is updated as the security landscape
changes and as better authentication methods emerge.
Temporary Access Pass
A one-time passcode that is generated and sent to the user via email or SMS.
- FIDO2 security key
A physical security key that the user inserts into their computer or mobile device to authenticate.
- Microsoft Authenticator push notifications
A notification that is sent to the user's Microsoft Authenticator app. The user can then approve the sign-in attempt from their app.
- Time-based one-time password (TOTP)
A code that is generated by the user's phone or other device. The code changes every few seconds, making it difficult for attackers to guess.
- Telephony
A phone call or text message that is sent to the user. The user then enters a code from the call or text message to authenticate.
- Certificate-based authentication
A digital certificate that is installed on the user's computer or mobile device. The certificate is used to authenticate the user when they sign in.
Friday, July 7, 2023
Remove or Change a user's email alias in Office 365
StandardChange a user's email alias
Procedure:
Modifying the Email Alias:
Hybrid Setup Considerations:
Remove a user's email alias
Procedure:
Unlicensed Users:
Monday, June 19, 2023
Scheduling meeting with voting poll
StandardIt is now easy to schedule a meeting when external parties are involved in the same meeting.
Last year, Microsoft released a feature called 'Find Time,' but most of us are not aware of it, and some lack knowledge about the new feature. In this article, I will share all my findings on the scheduling poll available in Outlook.
We can schedule a poll in two locations:
- Calendar
- New email
Next, change the required details as per your needs.

After you create the poll, you will see it in the email or calendar request as shown below.
Check your calendar; you will see that your calendar has been tentatively booked for the selected time frame.
Once you receive the votes, you can select 'View Poll Results,' and it will open on the web (https://outlook.office.com/findtime/dashboard).
Tuesday, June 6, 2023
Cross-Tenant Synchronization
Standard- Calendar Cross-Tenant Synchronization: This feature allows for the synchronization of calendars between different tenants. It ensures that appointments, events, and important dates are shared and updated across multiple tenants.
- Collaboration Cross-Tenant Synchronization: With this feature, users from different tenants can collaborate effortlessly. It enables real-time collaboration enabling smooth teamwork and productivity across tenants.
- Application Access Cross-Tenant Synchronization: By enabling this feature, users from one tenant can seamlessly access and interact with applications and data from another tenant. It simplifies the process of sharing resources and enhances efficiency in cross-tenant workflows.
Calendar Cross-Tenant Synchronization
Manage ownerless Microsoft 365 groups and teams
StandardTo ensure smooth functioning within groups, it is essential for each group to have an owner responsible for managing membership and settings. Owners possess unique permissions, including the ability to modify group configurations. However, situations may arise when the owner leaves, leaving members in need of assistance to add a new owner. This can potentially disrupt the ecosystem, especially within Microsoft Teams.
To address this issue, one possible solution is to implement a system where an email notification is automatically sent to active group members when there is no owner present. The email would request one of the active members to step up and become the new owner. This process can be facilitated through the following steps:
- Log in to the O365 admin center.
- Navigate to the Settings section.
- Locate the Microsoft 365 Groups option.
- Enable the functionality to identify ownerless groups by ticking the corresponding checkbox.
By implementing this option, the system will proactively identify groups without owners. This will trigger an email notification to active group members, alerting them to the vacancy and asking for someone to assume the ownership role. This approach ensures continuity and prevents the ecosystem from breaking due to lack of ownership.
By following these steps, you can improve the management of groups within Microsoft Teams, promoting a seamless experience for all members and maintaining the integrity of the ecosystem.
Friday, May 19, 2023
Which Authentication is the best Authentication?
StandardIn the O365 login page, we log in with our username and password. Is this secure?
I have seen multiple incidents where our clients complain that their accounts have been hacked. Someone has sent spam emails using their accounts and they have logged in from different countries, etc. If someone steals our password, what will happen? Let's see what authentication mechanisms are available to us and the benefits of using them.
Password: Passwords can be stolen through keyloggers. To protect ourselves, we can increase the password length, add characters and symbols, and increase password history.
PIN: For PC login, we can use a PIN instead of a password. PINs are more secure than passwords because they are easy to remember and unique to one device. Even if a PIN is stolen, the potential damage is much lesser than a compromised password.
Text Message or Voice Call: This method is more secure than a PIN or password because we receive a real-time code from the authentication service that is valid for a certain time period. A few years ago, I personally told my customers that two-factor authentication using text or voice call was the secure method to safeguard our users. However, this method is not valid nowadays as text messages or voice calls can be accessed through third-party applications.
Biometric or Face ID: Compared to the previous three methods, this is the most secure way because it requires your fingerprint or face to authenticate. This method is unique to you only.
Authenticator App: The Microsoft Authenticator app is one of the most secure apps we can use for authentication. You can set up biometric or Face ID to access applications.
Which is the newest method and most recommended by security experts?
"Go with PasswordLess"
How do we authenticate with passwordless?
You can select passwordless as your main authentication method. When you enter your username, it will automatically redirect and ask you to enter a number on your Authenticator app. To log in, you will not need a password, but you will need your mobile Authenticator app and biometric or Face ID. It will show you the location and application that is trying to authenticate.
.png)